Rust-for-Malware-Development
API Hooking using Trampoline
Explanation
The System API Interceptor is a Rust-based utility for intercepting and monitoring Windows API calls, specifically targeting the MessageBoxA function in user32.dll. It employs inline function hooking via a trampoline to redirect calls to a custom handler, log parameters, and invoke MessageBoxW with modified text.
d
How It Works [Step-By-Step]
- Interceptor Structure (
ApiInterceptor):- Stores the target function address (
MessageBoxA), replacement function address, original code bytes, and original memory protection state. - Uses a fixed-size array (
INTERCEPTOR_SIZE) for storing original bytes (14 bytes for 64-bit, 5 bytes for 32-bit).
- Stores the target function address (
- Setup (
setup_interceptor):- Resolves
MessageBoxAaddress usingGetModuleHandleAandGetProcAddress. - Copies the first
INTERCEPTOR_SIZEbytes ofMessageBoxAto preserve the original code. - Changes memory protection to
PAGE_EXECUTE_READWRITEusingVirtualProtectto allow code modification.
- Resolves
- Activation (
activate_interceptor):- Constructs a trampoline to redirect execution:
- 64-bit: Uses
jmp [rip+0](6 bytes) followed by an 8-byte absolute address of the custom handler. - 32-bit: Uses
jmp <relative>(5 bytes) with a relative offset to the custom handler.
- 64-bit: Uses
- Writes the trampoline to the
MessageBoxAentry point, ensuring minimal instruction overwriting.
- Constructs a trampoline to redirect execution:
- Custom Handler (
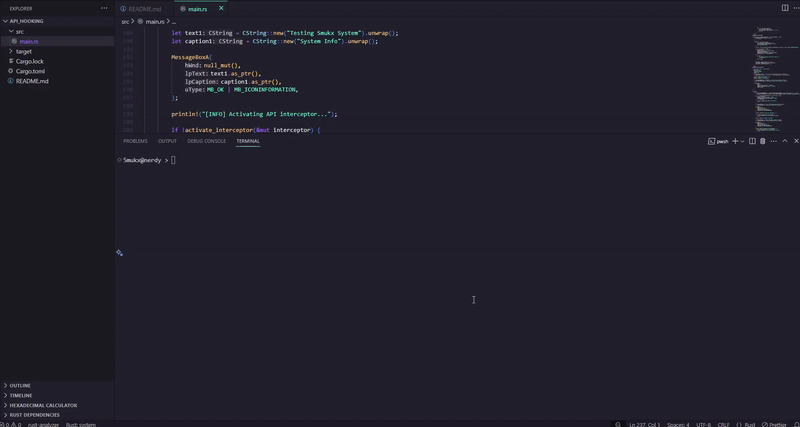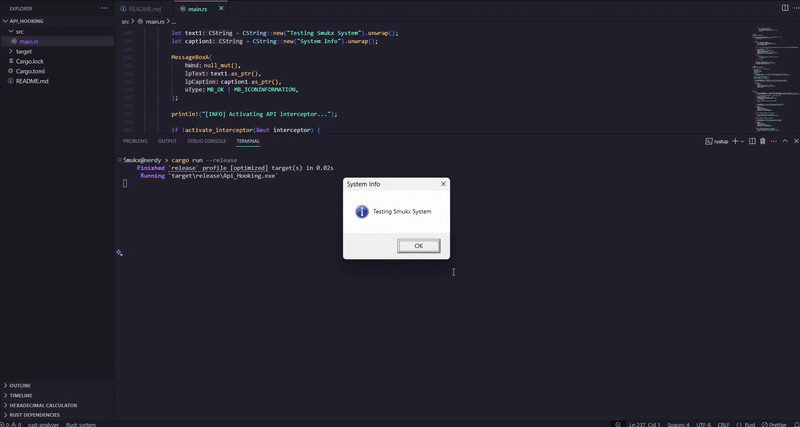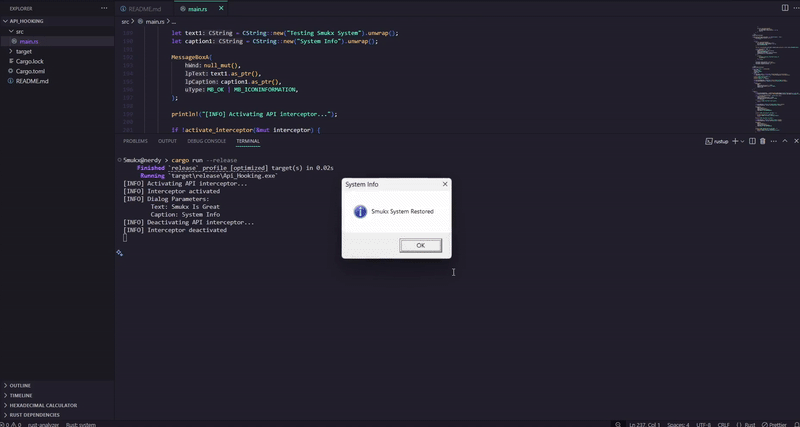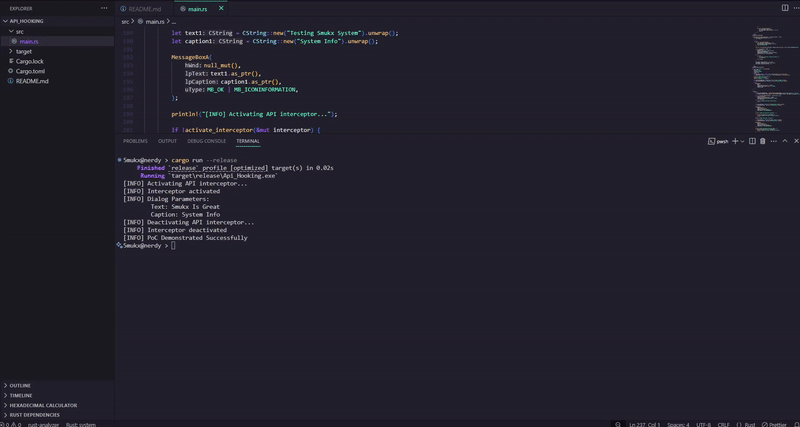
custom_dialog):- Logs input parameters (
lpText,lpCaption) usingCStr::to_string_lossy. - Converts new text to UTF-16 using
WideCStringforMessageBoxW. - Calls
MessageBoxWwith modified text (“Smukx Is Good”) and caption (“System Dialog”).
- Logs input parameters (
- Deactivation (
deactivate_interceptor):- Restores the original
MessageBoxAbytes from the stored copy. - Reverts memory protection to its original state using
VirtualProtect. - Clears the interceptor structure to prevent reuse.
- Restores the original
- Safety Considerations:
- Uses
unsafeblocks for WinAPI calls and pointer operations, ensuring controlled access. - Validates pointers and handles errors from WinAPI functions (e.g.,
GetLastError). - Maintains thread safety by avoiding shared mutable state.
- Uses
Key Features
- Cross-Architecture: Adapts trampoline construction for 32-bit and 64-bit systems.
- Non-Invasive: Preserves original function behavior during deactivation.
- Error Handling: Checks for null pointers and failed WinAPI calls.
- Logging: Outputs parameter details for debugging and monitoring.
How to Compile and Use It
- Compilation:
- Build:
cargo build --release. - Output:
target/release/Api_Hooking.exe.
- Build:
- Execution:
- Run:
target/release/Api_Hooking.exe. - Behavior:
- Displays an initial
MessageBoxAdialog. - Activates interceptor, showing a modified
MessageBoxWdialog. - Deactivates interceptor and shows a final
MessageBoxAdialog. - Exits on Enter key press.
- Displays an initial
- Run as administrator if memory protection changes fail.
- Run:
- Download the Snippet: Download
Credits
- https://github.com/ZeroMemoryEx/TrampHook
- https://www.ired.team/offensive-security/code-injection-process-injection/how-to-hook-windows-api-using-c++
- https://www.packtpub.com/en-us/product/mastering-malware-analysis-9781789610789/chapter/inspecting-process-injection-and-api-hooking-6/section/inline-api-hooking-with-trampoline-ch06lvl1sec86